Intelligent security for the modern workplace
Unique Risk-based Identity Protection: Helps prevent the use of compromised accounts using industry leading machine learning-based real time detection and automated mitigation, helping protect cloud and on-premises applications integrated with Azure AD. Microsoft has a unique differentiation in this area because we run many of the world’s largest cloud services, including Skype, Outlook.com, Xbox Live, Office 365 and Azure and they generate an incredible amount of data related to authentication, attacks and compromise attempts. This data along with other signals we collect from partners, Digital Crime Unit, and academia is put to good use! Every day our ML system processes >10 terabytes of data. All this intelligence results in calculation of a user risk level and real time login risk scores for every authentication request. Conditional Access policies uses these scores to automatically respond to threats as described below.
Conditional Access: In combination with the above risk-based identity protection, this is the most important capability that makes Microsoft’s offer unique. The ability to create access rules based on conditions such as user, location, device state and most of all risk level gives you the flexibility needed to allow access to applications from anywhere but still stay compliant and secure. Azure Active Directory Conditional Access can apply controls that block or allow access to apps , enforce compliance via Terms of Use acceptance requirements, or request 2-step authentication via Azure and 3rd party MFA providers
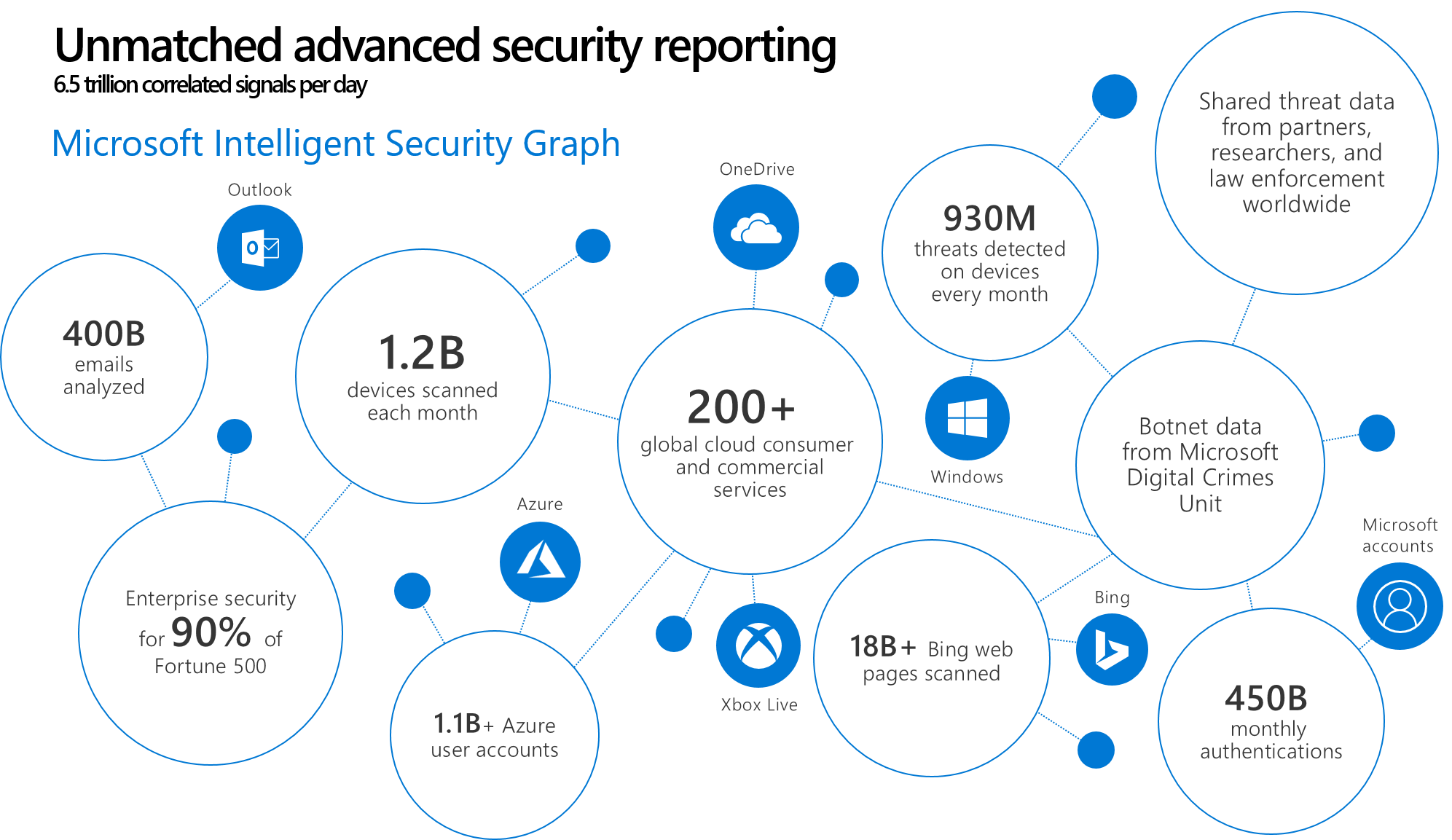
The center piece of our investment in intelligence is the Microsoft Intelligent Security Graph. This is how we describe the way that we synthesize a vast amount of data from a huge variety of sources. 400 billion emails get analyzed by our Outlook.com and Office 365 email services every month.
1.2 billion devices get scanned every month by Windows Defender. That gives us a great deal of signal into what's happening on endpoints, and where are the attacks, and what do they look like these days?
We operate 200-plus global cloud, consumer, and commercial services. Everything from outlook.com to Xbox Live to Office 365 to Azure, and so on. And with all of those services, we have a tremendous amount of surface area that we defend. Enterprise Security from Microsoft is employed by 90% of the Fortune 500.
And so, we see more attacks than most other companies on any given day. We get a lot of information from defending against those attacks.
750 million plus Azure user accounts give us tremendous insight into how people authenticate to Azure. And that, combined with the 450 billion monthly authentications that we do with Azure Active Directory and Microsoft Account, really give us some tremendous insight into what is normal behavior when it comes to sign-ins and authentications, and what is abnormal behavior, and how often is it that someone has the right password, but they're not the person they say they are. We learn a lot about defending that really important control point, the identity, by looking across that set of data.
Bing scans about 18 billion web pages every month, giving us really great insight into what people are doing with web scripting technologies when it comes to attacks and phishing campaigns. And we have a great way to look at that and understand how we should help customers defend based on that information.
On top of all of that we layer shared threat data that we get from our partners, from the researchers here at Microsoft who are part of our 3,500-plus people that are full time on security, and law enforcement agencies that we partner with worldwide through our digital crimes unit, as well as botnet data that we collect through the digital crimes unit. All of that intelligence makes up the Intelligent Security Graph.
And why is it a graph? It's a graph because what's really important is connecting these pieces of intelligence, so that these signals are not just individual points of information. The graph brings them together as something that we can draw patterns across. We can learn from one point of data to influence how we interpret another point of data.
So, the Intelligent Security Graph is something that we are very, very heavily invested in at Microsoft. It's something that we feel is unique to us in this industry.